Many consumer IoT companies failing to adopt fundamental security measures despite the threat of legislation and regulation
Latest report finds that providers of consumer IoT are less likely to have a readily detectable vulnerability disclosure policy in place than firms operating in the business-to-business space.

Published today (4 November 2021), the latest IoT Security Foundation (IoTSF) report examining the adoption of vulnerability disclosure in IoT – commissioned by the IoTSF and prepared by Copper Horse – finds little improvement on last year’s figures. The overall trend, while moving in the right direction, remains far short of what’s needed to bolster confidence in the security of IoT products. Given the persistently slow pace of voluntary adoption, regulatory wheels have started turning to force companies to think more seriously about their vulnerability disclosure processes.
2021 headlines
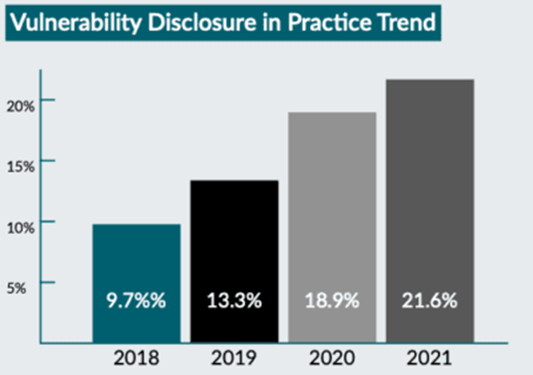
- The adoption of vulnerability disclosure in the IoT sector remains unacceptably low (just 21.6% of firms surveyed had a readily detectable policy in place). Based on these findings, almost 4 out of 5 companies are failing to provide the very basic security hygiene mechanism to allow security vulnerabilities to be reported to vendors so they can be fixed.
- The slow pace of vulnerability disclosure adoption by IoT providers continues to put users at risk by failing to maximise the opportunity to close gaps in product security (the percentage of firms surveyed with a readily detectable policy in place is up just 2.7% on findings for 2020).
- Anticipating forthcoming legislation, only 21 out of the more than 300 IoT providers surveyed would meet modest regulatory requirements.
- Business-to-business IoT providers are much more likely to have a readily detectable policy in place compared with firms operating in the consumer sector.
- Lack of information is no longer an excuse for IoT providers as best practice guides have been updated and new tools made available to streamline putting a vulnerability disclosure policy in place.
Security benefits are too good to ignore
Reporting a product security issue should be made simple so that a vendor can get to work on investigating and developing a fix as soon as possible. Coordinated Vulnerability Disclosure (CVD) policies cover all stages of the process from advertising the correct point of contact, through to the timescale for fixing any issues and recognition for any bugs discovered.
Vulnerability disclosure, backed by a Vulnerability Disclosure Programme (VDP), benefits multiple parties – governments, businesses, security researchers and customers – so much so, that the process is well on its way to becoming a mandatory requirement at an international level.
Free guides and online tools
2021 has seen a jump in the provision of information to help firms, which includes the IoTSF’s updated Best Practice Guide and a time-saving policy-maker tool, developed by disclose.io. More details and links can be found in the report.
Legislative wheels are turning
With governments around the world turning to legislative and regulatory means to tackle the lack of improvement in the market, it is surprising to us that there hasn’t been an increase in the rate of adoption of CVD, particularly in the last year. These companies will find it difficult to sell their products if they don’t change their ways, and soon.
David Rogers, the CEO of Copper Horse said, “The report provides measurable evidence of IoT manufacturer and brands’ lax attitudes towards security in general. There is nowhere to hide for these companies – international standards are there to be used and coordinated vulnerability disclosure is recognised good security practice. The question for consumers globally is: ‘why should I buy products from these companies if they don’t look after security?’”


